General Data Protection Regulation or GDPR is all about privacy. If a company handles privacy in the right way, then it can dodge penalties like 20 million Euro or 4 % of the worldwide revenue.
Time for a legal break. Right after this break some idea.
Disclaimer
I am not a legal expert. So please have a look at my used sources. Or contact a GDPR expert.
I am just a tester finding test ideas about GDPR. Thanks for joining in advance.
The following story has been sanitised by me. Important details have been changed.
Bad idea
The job interview was about an agile tester. I thought I could handle that role. The probing questions from the interviewers were increasing. I tried to stay calm and answer the questions in a friendly way.
Then came the expected question about test cases. They should be written beforehand. Time to explore.
“You never know what you will find.”, I remarked.
“Let me give me an example.”
“Your company sent me this mailing.”
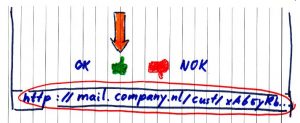
I showed a part of the mail.
“At the bottom of the mail I could say, whether I like this mail.”
There were two pictures: one green thumb up and one red thumb down. There was an orange arrow pointing to the thumb up.
“If I hover above the picture of the green thumb, the URL will be shown in the status bar of the mail.” The URL was contained in a red eclipse.
“As you notice: the URL is http. This is not secure. If the mail is intercepted, then the reaction of the customer can easily be determined. This is an email about credit, so you can derive that the customer probably has some debts.”
One of the interviewers politely interrupted me:
“Is it possible to intercept mail?”
I gave a technical answer using normal words.
Okay, I got his attention.
Then the exploratory tester awoke in me. And I could not stop him.
“There is a customer number in the mail. This number can be used to get access to an online account.”
I went in full brainstorm mode and described all kinds of product risks or things which could harm the user. I could find information about correspondence about money.
I didn’t get the job, but the mailing was fixed afterwards. Obviously 20 million Euros are not enough to qualify as a tester.
But there are retrospectives for.
[On the melody of ‘That’s What Friends Are For’.]
Breakdown
Most of the time primary systems were and are tested for GDPR and national privacy laws. Sometimes this software did not easily support mailings. An easy solution was to use another system outside the company. Specialised in mailings.
All kinds of data like email addresses, names, and profiles were used for mailings. Technical decisions were taken like http instead of https. Somehow the legal department and testers missed something.
According to GDPR the protection of personal data is a fundamental right [ (1) on page 1]. The economic situation of a person can be used for profiling. In turn this can be used to exclude people to get certain services like mortgage [ (75) on page 15].
My tips for testing:
- become a customer of your own company and use all available channels. Watch for the legal details like the missing s of https. (See last tip)
- follow security experts on social media. (You know about the last tip)
- explain legal and security stuff in normal words.
- let the owner control the flow of information. I should have send my brainstorm on request.
- read ‘Here’s Why Your Static Website Needs HTTPS’ by Troy Hunt, a security researcher. It contains an entertaining 25 minute video with several attacks on an http website.
For people new to security, just watch the video and focus on what you would not like to happen on your website.
Closing note:
At the moment there are browsers showing whether a website is insecure. This was not the case, when I received this mailing.
To be continued.